- Malware Detection
- Dynamic Behavior Analysis
- Integration of Various AI Technologies
- Support for Large-Scale Malware Databases
- YARA Support Implementation
- Rapid Malware Identification
- High Availability and Scalability
- Multi-Endpoint Forensic Collection and Correlation Monitoring
eDetector is a cutting-edge endpoint digital forensic and evidence collection system designed for cybersecurity investigations, honored with multiple awards, including the Small Business Innovation Research (SBIR) program of the Ministry of Economic Affairs.
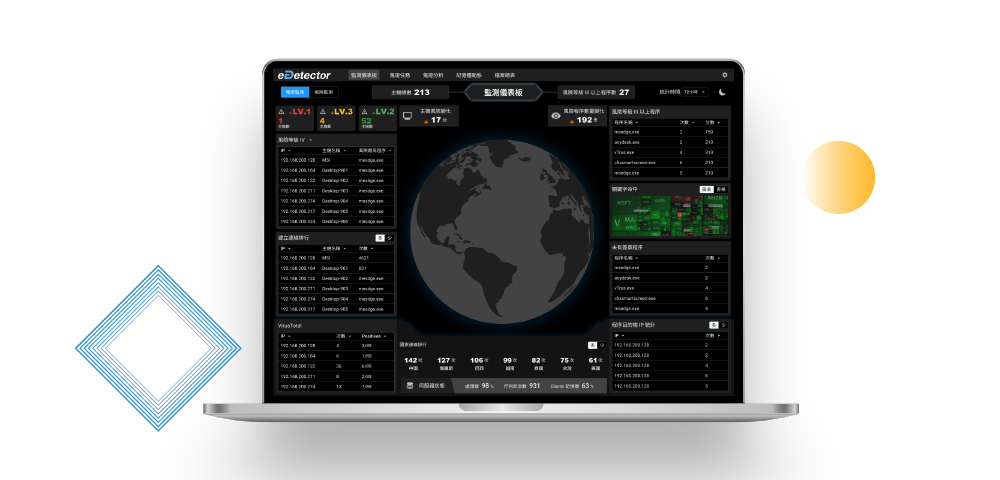
By combining memory detection and behavioral artifact analysis, eDetector quickly identifies malicious activities such as code injection, hidden programs, core interception, and connection history. It detects suspicious actions and provides root cause analysis of attacks. The system also generates process correlation maps and marks source IPs, helping users gain a comprehensive view of incidents.
Flyer


- Supports the collection of over 40 types of digital evidence, including browser history, USB device information, program network traffic, DNS information, and Windows activities.
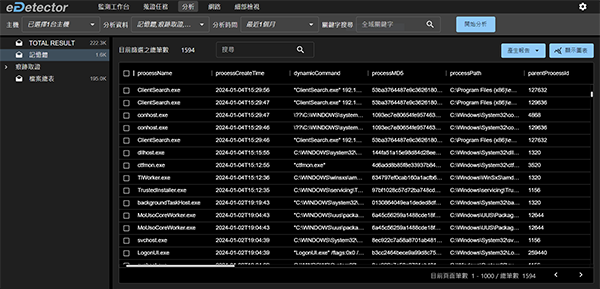
- High-speed search capabilities allow scanning of millions of records within seconds, providing real-time file listings and dynamic data retrieval.
- Integrates AI technology and the VirusTotal database to generate rapid analysis reports, capturing malware characteristics and source information.
- Supports dynamic detection of unknown malware, identifying potential threats through memory analysis and behavior tracking.
- Provides process tree diagrams, loaded module and DLL lists, and marks program connections and source IPs for quick identification of malicious activities.
- Integrates Yara scanning technology to efficiently filter malware characteristics and pinpoint potential risks.


- Provides stable cloud services with flexible storage expansion, ensuring data confidentiality, integrity, and availability.
- Security personnel can monitor cross-machine operations and manage task progress via a web interface, enhancing operational convenience.
- The visualized timeline feature allows for quick review and analysis of data insights.